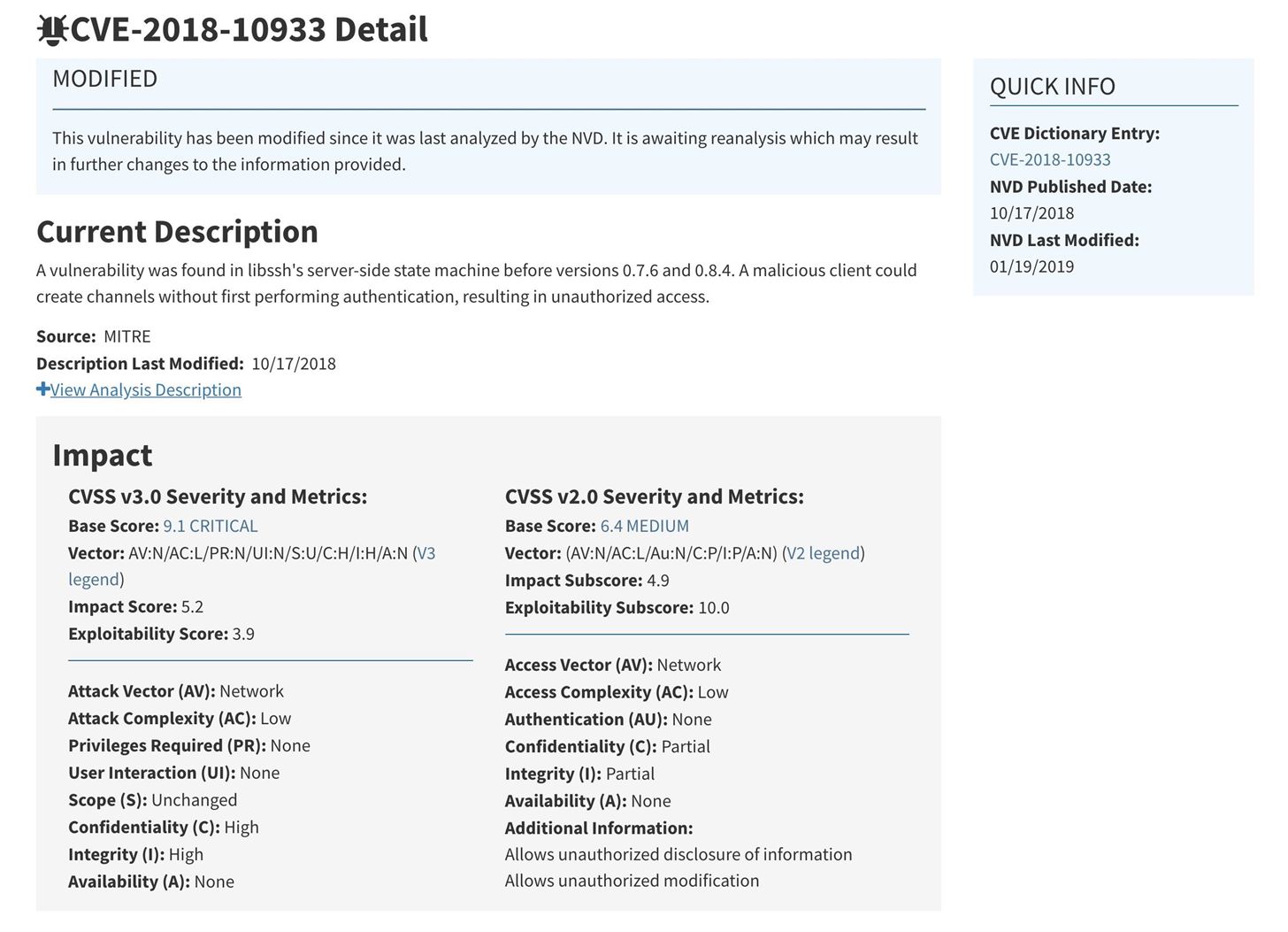
Install Nikto
How To Install Nikto Web Scanner To Check Vulnerabilities in UBUNTU Nikto Web-scanner is a open source web-server scanner which can be used to scan the web-servers for malicious programs and files. Nikto can be used to scan the outdated versions of programs too.
Nikto performs more than 6700 tests against a site. The vast number of tests for both security vulnerabilities and mis-configured web servers makes it a go to device for most of the security experts and pentesters. Nikto can be used to test a Web Site and Web Server or a Virtual Host for known security vulnerabilities and mis-configurations of files, programs and servers. It can discover overlooked contents or scripts and other difficult to identify issues from an outside point of view.
Installation
Installing Nikto on Ubuntu system is basically straightforward as the package is already accessible on the default repositories.
First to update the system repositories we will use the following command :
After updating your system. Now Run the following command to Install Nikto.
After the completion of installation process ,use the following command to check if nikto is installed correctly or not :
- Nikto v2.1.6
------------------------------------------------------------
If the command gives the version number of Nikto it means installation is successful.
Usage
Now we are going to see how we can use Nikto with various command line options to perform web scanning.
Generally Nikto requires just an host to scan which can be specified with -h or -host option for example if we need to scan a machine whose ip is 192.168.30.128 we will run Nikto as follows and the scan would look something like this:
- Nikto v2.1.6
------------------------------------------------------------
+ Target IP: 192.168.30.128
+ Target Hostname: 192.168.30.128
+ Target Port: 80
+ Start Time: 2020-04-1110:01:45(GMT0)
------------------------------------------------------------
+ Server: nginx/1.14.0 (Ubuntu)
..snip..
+ /: A Wordpress installation was found.
+ /wp-login.php: Wordpress login found
+ Apache/2.4.10 appears to be outdated
+ The X-XSS-Protection header is not defined. This header can hint to the user agent
to protect against some forms of XSS
+ Server may leak inodes via ETags
------------------------------------------------------------
+ 1 host(s) tested
This output has a lot of useful information .Nikto has detected the Webserver, XSS vulnerabilities, Php information and WordPress installation.
OSVDB
The items in a nikto scan with OSVDB prefix are the vulnerabilities that are reported in Open Source Vulnerability DataBase (similar to other vulnerability databases such as Common vulnerabilities and exposures, National Vulnerability Database etc).These can come in quite handy based on their severity score ,
Specifying Ports
As you can see from above results, when the port is not specified Nikto will scan port 80 by default . If the web server is running on a different port, you have to specify the port number by using -p or –port option.
- Nikto v2.1.6
------------------------------------------------------------
+ Target IP: 192.168.30.128
+ Target Hostname: 192.168.30.128
+ Target Port: 65535
+ Start Time: 2020-04-1110:57:42(GMT0)
------------------------------------------------------------
+ Server: Apache/2.4.29 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ Apache/2.4.29 appears to be outdated
+ OSVDB-3233: /icons/README: Apache default file found.
+ Allowed HTTP Methods: OPTIONS, HEAD, GET, POST
1 host scanned..
From the above information we can see that there are some headers that help indicate how the website is configured. You can get some juicy information from secret directories too.
You can specify multiple ports by using comma like:
Download fifa 2002 game free. Download Fifa 2002 Game Overview. Fifa 2002 PC Game is an open-world action-adventure game developed by EA Vancouver. It was released on October 29, 2001 for the PlayStation, Microsoft Windows, Xbox and all other well known operating systems.
Or you can specify a range of ports like:
Using URLs to specify a target host
To specify the target by its URL we will use a command :
Nikto scan results can be exported in different formats like CSV, HTML, XML etc. To save results in a specific output format, you need to specify the -o (output) option and also the -f (format) option.
Example :
Now we can access the report via browser
Tuning parameter
Another decent component in Nikto is the likelihood to characterize the test utilizing the – Tuning parameter. This will let you run just the tests you need which can spare you a great deal of time:
- File upload
- Interesting files/logs
- Mis-configurations
- Information disclosure
- Injection(XSS etc)
- Remote file retrieval
- Denial of service (DOS)
- Remote file retrieval
- Remote shell – Command execution
- SQL Injection
- Authentication Bypass
- Software identification
- Remote source inclusion
- Reverse tuning execution (all except specified)
For example to test for SQL injection and Remote file retrieval we will write following command :
Download the latest drivers, firmware, and software for your HP H7000 Bluetooth Wireless Headset.This is HP’s official website that will help automatically detect and download the correct drivers free of cost for your HP Computing and Printing products for Windows and Mac operating system. Cechya-0075 ps4. RanvirSingh Created on September 9, 2012 SLEH-00075 headset driver fails to install with the error “The drivers for this device are not installed. Its says the drive for the device is installed (code 28) so how do i install it. View and Download Sony SCEH-00075 user manual online. Sony Headphones User Manual. SCEH-00075 Headsets pdf manual download. Also for: Sceh-00087, Playstation 3 sceh-00075, Playstation 3 sceh-00087.
Pairing scans with Metasploit
One of the coolest things about Nikto is that you can pair the output of a scan with Metasploit readable format. By doing this you can use the output of Nikto in Metasploit to exploit the particular vulnerability. To do so, just use above commands and append -Format msf+ to the end. It will help quickly pair data retrieved with a weaponized exploit.

CONCLUSION
Nikto is a famous and simple to utilize web server assessment tool to discover potential issues and vulnerabilities rapidly. Nikto ought to be your first decision when pen testing web servers and web applications. Nikto is filtering for 6700 possibly risky documents/programs, checks for obsolete forms of more than 1250 servers, and adapts explicit issues on more than 270 servers as indicated by the authority Nikto site. You should know that using nikto isn’t a stealthy procedure means that an Intrusion Detection System can easily detect it. It was made for security analysis, so stealth was never a priority.